A recent social engineering campaign has been discovered targeting individuals seeking employment in the Web3 industry. Attackers lured job seekers into fake interviews using a fraudulent meeting application called “GrassCall,” which, once installed, deployed malware designed to steal cryptocurrency wallets and sensitive user data.
Reports indicate that hundreds of individuals were affected by this scam, with some victims experiencing complete drainage of their crypto wallets. In response, a Telegram group has been established to facilitate discussions among affected users and provide assistance in removing the malware from both Windows and Mac devices.
Organized Cybercriminal Group Behind the Attacks
The campaign was orchestrated by a Russian-speaking cybercriminal group known as Crazy Evil, specifically by a subgroup referred to as “kevland.” This group is known for executing social engineering strategies to deceive individuals into installing malicious software. Previously, they have targeted users in the cryptocurrency sector by promoting fraudulent games and job opportunities through social media channels.
The scam involved the creation of an elaborate online presence, including a fabricated company named “ChainSeeker.io.” The perpetrators established a website and multiple social media profiles on platforms such as LinkedIn and X to lend credibility to their deception. To attract job seekers, the attackers posted premium job listings on reputable job platforms like LinkedIn, WellFound, and CryptoJobsList, which are commonly used for Web3 and blockchain-related career opportunities.
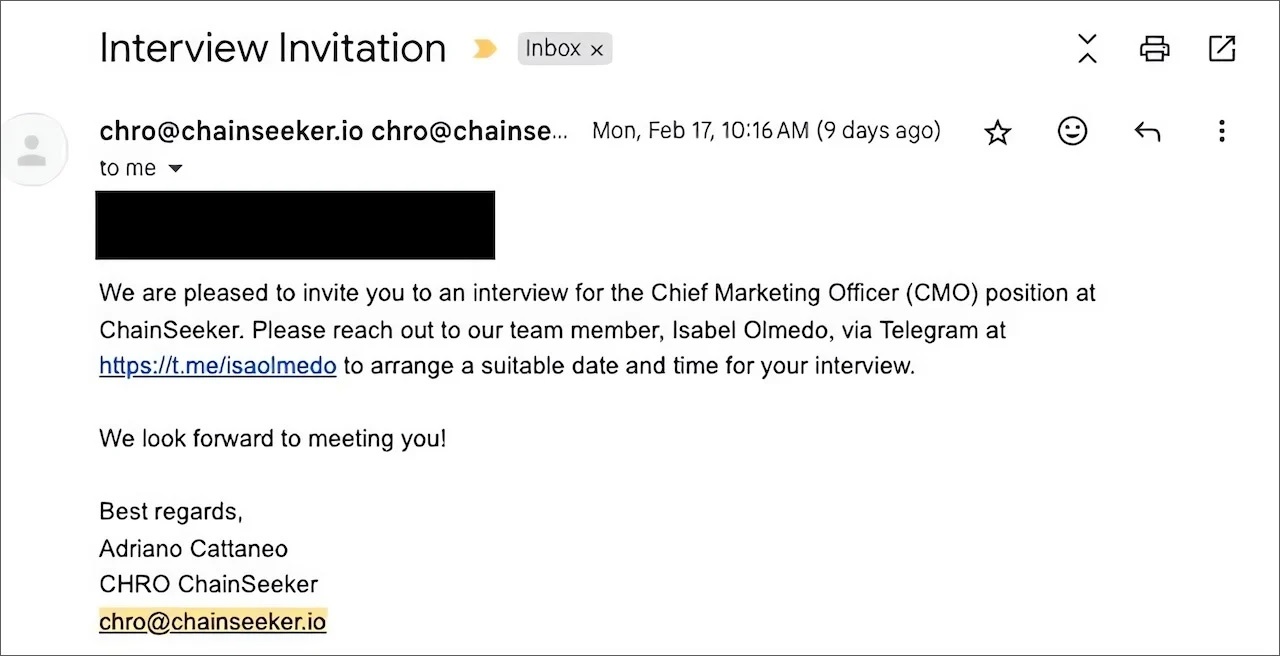
Applicants who responded to these job postings were subsequently contacted via email and invited to participate in an interview with a supposed Chief Marketing Officer (CMO). As part of the communication, the victims were instructed to reach out to the CMO via Telegram to coordinate the interview details. Once engaged, the fraudulent CMO directed the job seekers to download the “GrassCall” video conferencing software using a provided website and an access code.
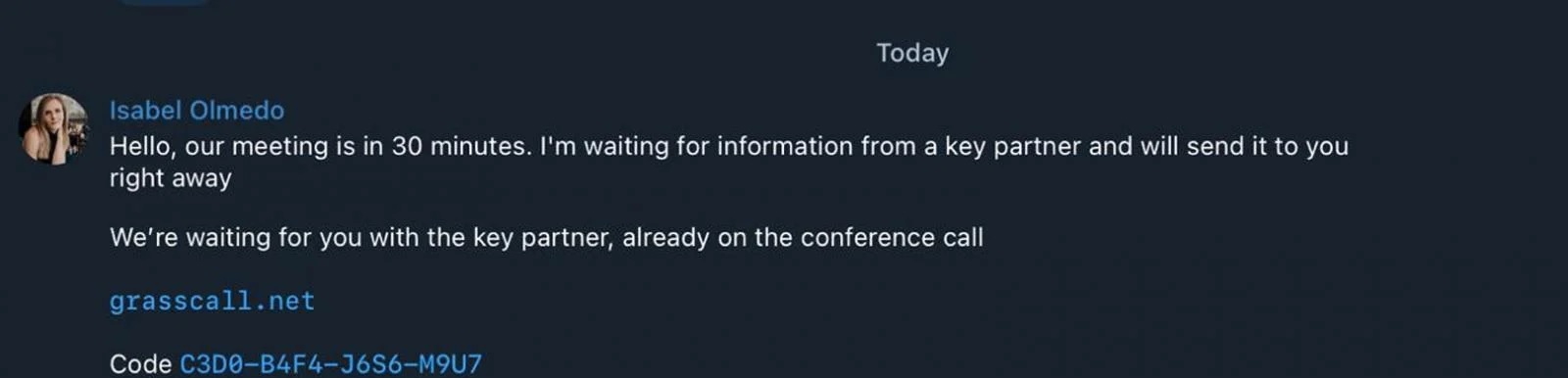
Malware Deployment and Data Theft
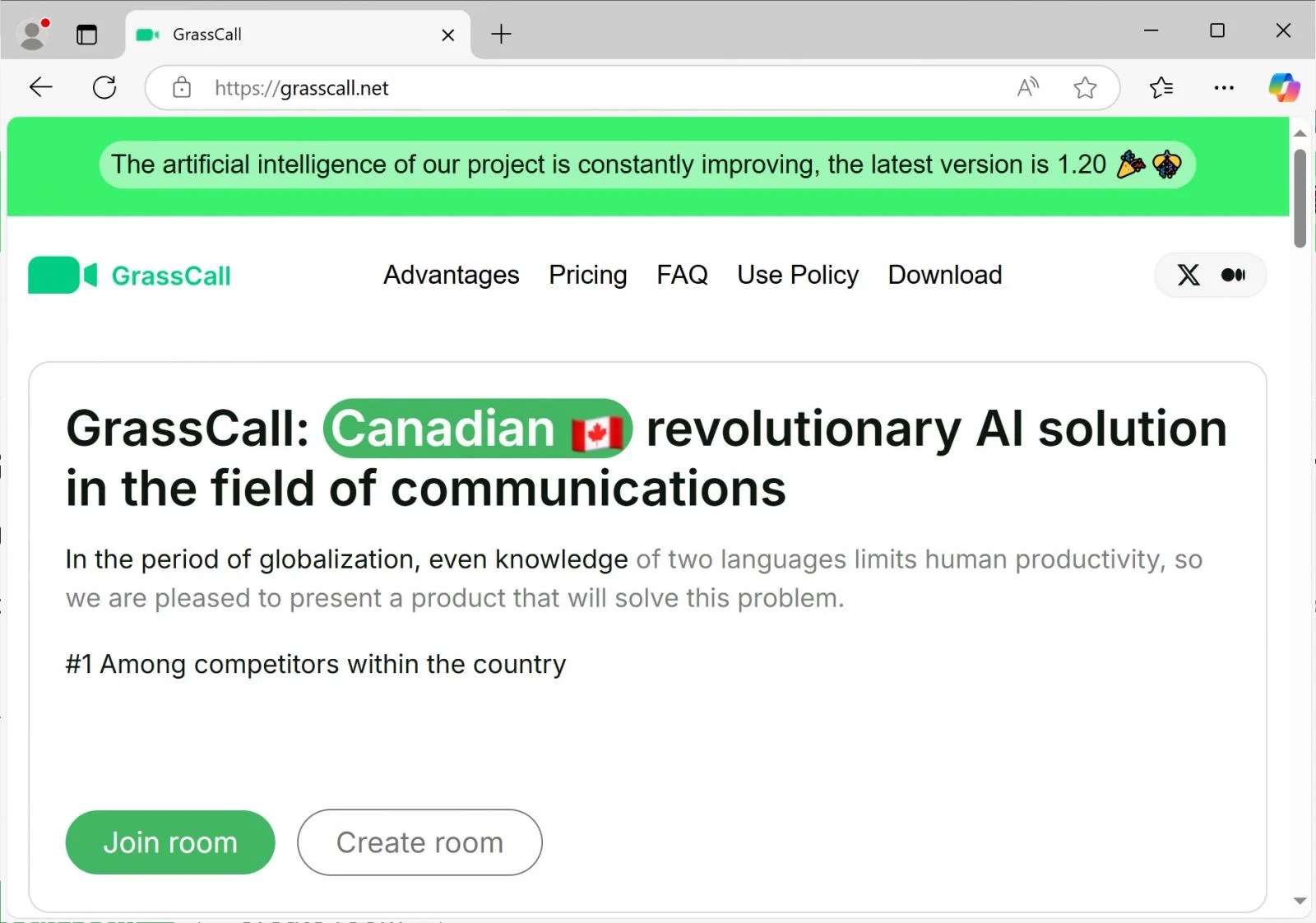
The GrassCall software was hosted on “grasscall[.]net,” a site that detected the visitor’s browser user agent to determine whether to offer a Windows or Mac download. Cybersecurity researchers tracking these activities have identified that the GrassCall website is a clone of a previous fraudulent meeting platform, “Gatherum,” which was also used for similar scams by the same criminal group.
When the targeted users entered the access code and installed the GrassCall application, their devices became infected with information-stealing malware. On Windows systems, a remote access trojan (RAT) was deployed alongside an infostealer, such as Rhadamanthys. Mac users, on the other hand, were targeted with the Atomic (AMOS) Stealer malware.
Researchers analyzing these attacks have indicated that the RAT is used to establish persistent access to the infected machine, deploy keyloggers to capture passwords, and initiate phishing attempts aimed at extracting seed phrases from crypto wallets. Once executed, the malware scans for files associated with cryptocurrency wallets, stored passwords, and authentication cookies from web browsers. The stolen data is then uploaded to the attackers’ servers, and details of compromised accounts are shared within private Telegram channels used by the criminal organization.
Financial Incentives for Cybercriminals
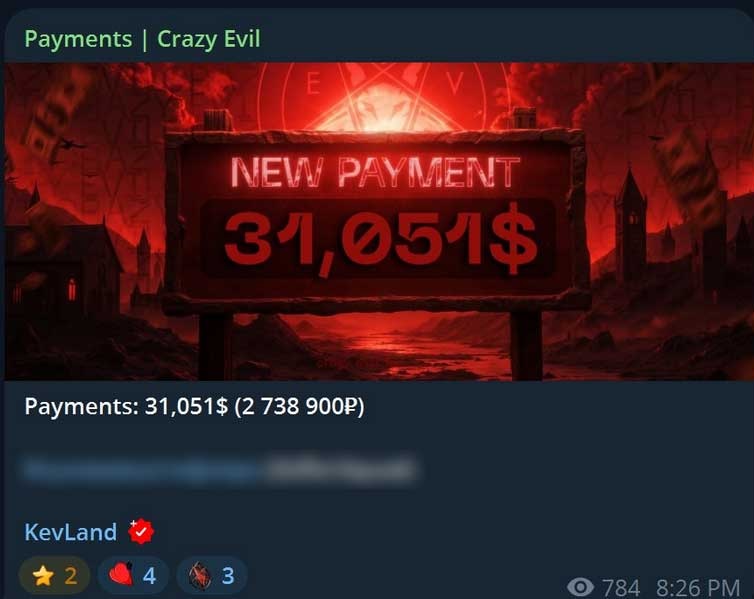
Investigations into the operation have revealed that members of the Crazy Evil group receive financial rewards based on their success in compromising victims. When a cryptocurrency wallet is identified, attackers attempt to brute-force passwords to access the assets. Once the funds are stolen, payments are distributed to the criminals who managed to trick the victim into installing the software. Evidence shared on Telegram suggests that some members of this group have earned substantial amounts, reaching tens or even hundreds of thousands of dollars per compromised target.
Response and Prevention Measures
Following the exposure of this scam, CryptoJobsList took immediate action by removing the fraudulent job postings and issuing warnings to those who had applied, advising them to conduct malware scans on their devices. Additionally, the malicious website associated with the campaign has since been taken offline, signaling that the perpetrators may have discontinued this particular operation.
Despite this, cybersecurity experts stress the importance of taking proactive measures for those who may have unknowingly installed the software. It is strongly recommended that affected users update all passwords, reset authentication tokens, and change passphrases for their online accounts and cryptocurrency wallets to prevent further security breaches.
As cybercriminals continue to refine their techniques, individuals in the Web3 space are urged to remain cautious when engaging with online job listings and video conferencing tools. Vigilance and verification of company legitimacy remain key in mitigating the risks associated with social engineering attacks.









